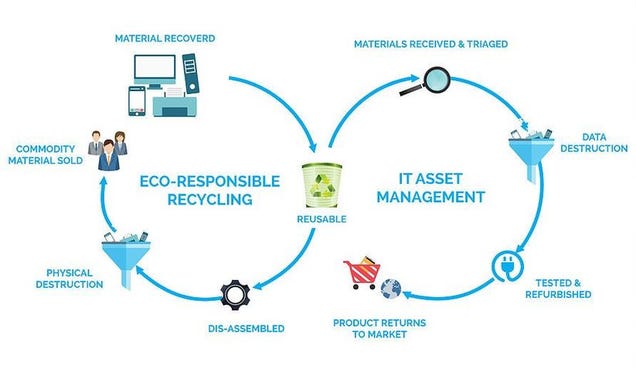
Data Destruction
Data security is needed for anyone, not merely the ones that are involved with data security because up to now, every computer has sensitive data inside, which could develop into a danger to anyone that has their computer sold, donated, or disposed. The reason being the common security measures that you do like deleting or formatting a drive isn't enough.
Issues With End-of-Life Data
Before this case was discovered, the safest solution to remove data is to delete or format the media. There is also little curiosity about the business about what'll happen if the disk containing sensitive information reached its end-of-life. When severe data loss occurred like in Equifax where a lot more than 2000 customer records were stolen. The records contain full credit information of 2000 records of consumers worldwide. Thus, data destruction is another issue that organizations must take attention.
During living of the data, https://assetrecovery.kinja.com/ava-e-recycling-1833012869 are spent in protecting the data. Computers are secured with a code, to prevent online hacking, it's protected with a firewall, and for safe storage of highly sensitive information, it's encrypted.
Almost none are spent in protecting the file when it reaches its end-life. This therefore becomes a vulnerability to an organization.
Determining the danger
Data Categories - Not All Data Are The Same
Data is categorized into various levels based on how it affects the business or company. Impact level is the quantity of threat at data may cause to the business or organization. Impact level 0 is the safest data. This information is already shared to the public via the web site or public records. Impact level 1 is all about the contact information of employees, for instance which are not in a public domain. Impact level 2 is the overall information of the business not proven to the public. Level 3 is the payroll, sales, and customer information. Level 4 is the customer's bank card details Level 5 are sales and cash flow forecasts Level 6 data are bank login information, strategic, and flotation plans.

These data categories have its corresponding risks like each time a data level 6 is stolen, an organization can lose as much as $100 million or cause an extreme threat to its country.
How To Determine and Perform Data Destruction
Data destruction can be achieved by either overwriting, degaussing, shredding, and disintegration. Every one of this approach has several levels of destruction where the larger the security risk of the data, the more severed the data destruction method is.
The strategy must be equal to the impact amount of the data to destroy to have effective data destruction.
Data Wiping
Data wiping is really a data destruction method wherein the file is overwritten repeatedly with 0s and 1s and is repeated repeatedly, so that it cannot be recovered using a data recovery software. Data wiping uses different wiping algorithms to overwrite the data.
Degaussing
Eliminating data via degaussing is the procedure of decreasing any unnecessary magnetic field leaving the drive into its original state. Degaussing reduces the magnetic flux of the drive by applying a slow magnetic field. For a push to be degaussed effectively, the degaussing machine must have twice the magnetism of the disk. This magnetism is measured as Oersted. If modern hard disks have 2000 Oersted, then the degaussing machine should have 4000 Oersted.
Shredding
Shredding is the fastest and most typical method to get rid of data on a hard disk drive. It is basically because shredding is really a physical destruction method. Imagine a hard disk which can be shred to pieces as if it were shredding a paper.
You will want to just shred everything?
Shredding hard disk is your last option if all the above option fails. Moreover, once the disk has been shredded, there it cannot be utilized again that's why you will need to shred disks only if it's inoperable or before you get rid of the drive.
You can't just destroy a hard disk, there are factors that really must be considered first like: Quantity of disks required for data destruction